Google has been very quick to identify and terminate the accounts of these malware advertisers, but what will their response be when long-time "known good" advertisers suddenly start having malware pop up in their ads?
This seems to be the focus of a new phishing campaign.
The email which comes from:
adwords-noreply@google.com
Looks like this:
Dear Google AdWords Customer!
In order to update your billing information, please sign in
to your AdWords account at https://adwords.google.com, and submit your
billing information. Your account will be reactivated as soon as you have
entered your payment details. Your ads will show immediately if you
decide to pay for clicks via credit or debit card. If you decide to pay
by direct debit, we may need to receive your signed debit authorization
before your ads start running, depending on your location. If you
choose bank transfer, your ads will show as soon as we receive your
first payment. (Payment options vary by location.)
Thank you for choosing AdWords. We look forward to providing you with
the most effective advertising available.
Sincerely,
The Google AdWords Team
The problem is that the Adwords link doesn't go to Google. In a review of fifty samples of the email collected from the UAB Spam Data Mine, fifteen counterfeit "Google AdWords" websites were identified:
http://adwords.google.com.049jfm.cn/select/Login/
http://adwords.google.com.0k8ujd.cn/select/Login/
http://adwords.google.com.adwordsgl.cn/select/Login/
http://adwords.google.com.fgreo3.cn/select/Login/
http://adwords.google.com.fnjdk.cn/select/Login/
http://adwords.google.com.fr4ck.cn/select/Login/
http://adwords.google.com.fri23.cn/select/Login/
http://adwords.google.com.fruwa0b.cn/select/Login/
http://adwords.google.com.googadw.cn/select/Login/
http://adwords.google.com.irf12.cn/select/Login/
http://adwords.google.com.kdje332.cn/select/Login/
http://adwords.google.com.ork0r.cn/select/Login/
http://adwords.google.com.r4oik.cn/select/Login/
http://adwords.google.com.session932.cn/select/Login/
http://adwords.google.com.treoo.cn/select/Login/
In what is now becoming a familiar pattern, criminals are using previous crimes to enable future crimes. In the current example of the Google Adwords phishing spam, although the "From" addresses say the email came from Google, the rest of the header makes it clear that these emails were sent from logged in Yahoo and Hotmail accounts.
Whether these accounts were created as throw away accounts for this spam campaign, or are actually accounts which were broken into and used without their owners' permission is still being investigated. The lists of yahoo and hotmail accounts have been shared with investigators, and those, as well as the counterfeit website lists, have been sent to the FBI's Digital PhishNet for further investigation.
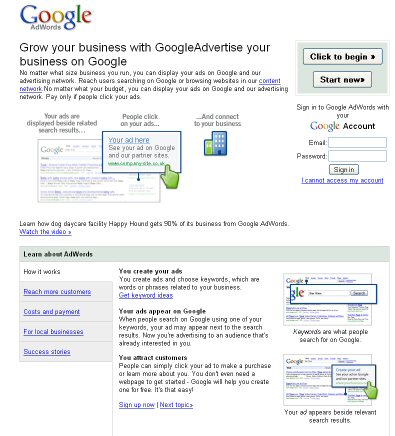
(screen shot of http://adwords.google.com.adwordsgl.cn/select/Login/ - 24MAR08 0630AM CST)
Emails were received from Brazil, Germany, India, the Netherlands, Russia, Spain, Switzerland, Turkey, Uruguay, but also from California, Florida, Georgia, Indiana, and Massachusetts.
The UAB Spam Data Mine is operated by UAB Computer Forensics Research, a Joint Operation of the Department of Computer & Information Sciences and the Department of Justice Sciences at The University of Alabama at Birmingham.






0 comments:
Post a Comment